Okta
Okta is a popular identity provider used by businesses of all sizes. Integrating Pomerium with Okta allows you to use the identity Okta provides to apply context-driven policies from Pomerium to your infrastructure.
This page covers configuring Okta to communicate with Pomerium as an IdP. It assumes you have already installed Pomerium before you begin.
While we do our best to keep our documentation up to date, changes to third-party systems are outside our control. Refer to Okta's developer docs as needed, or let us know if we need to re-visit this page.
Create OpenID Connect Application
-
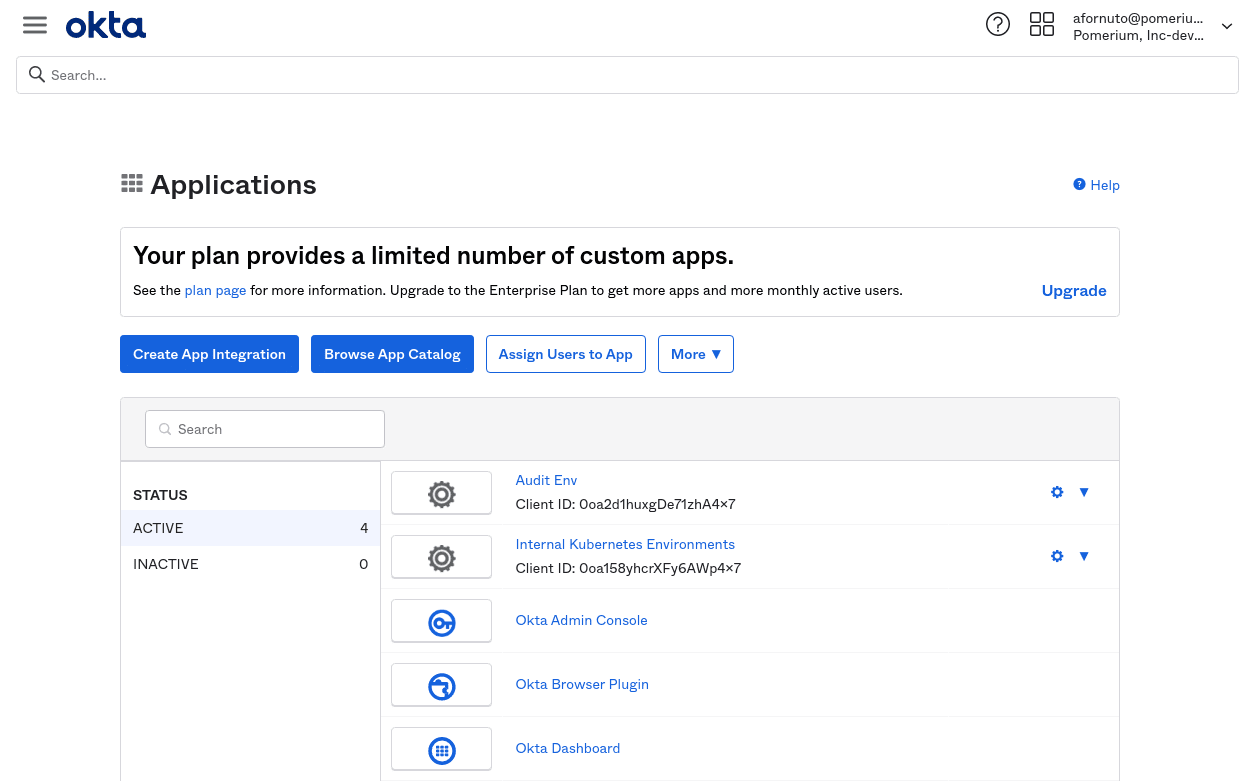
Log in to your Okta account From the left-hand menu, Select Applications → Applications on the top menu.
-
Click the Create App Integration button. Select OIDC as the sign-in method. and Web Application as the application type:
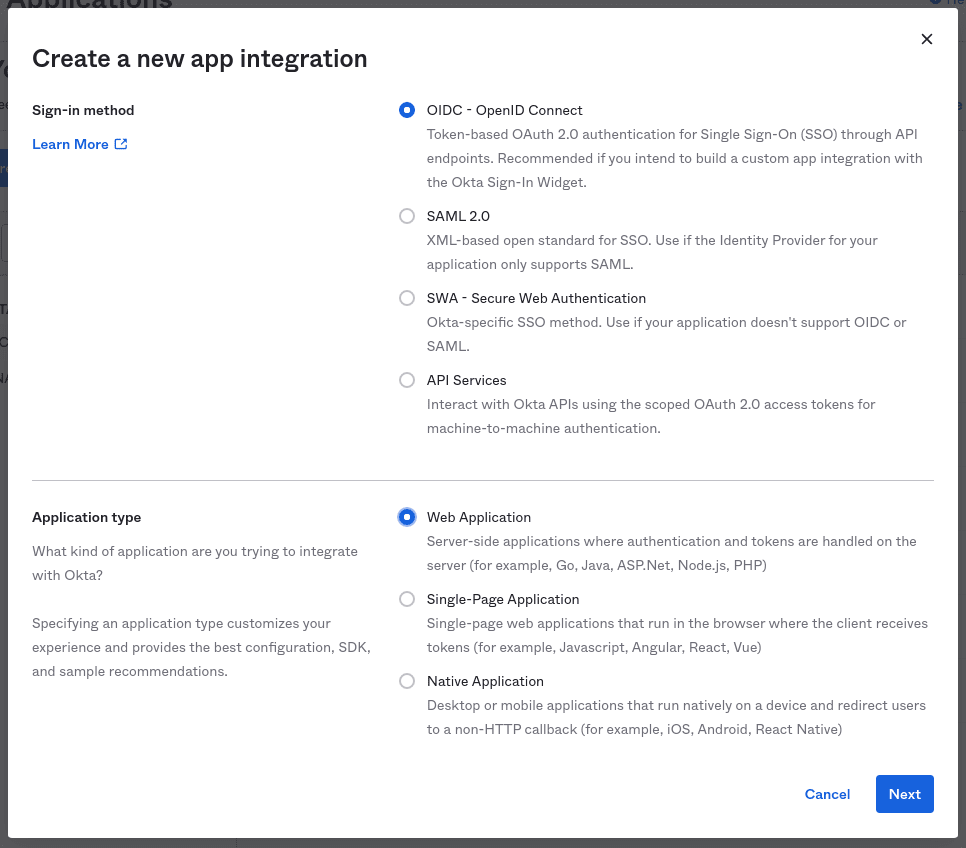
Click Next to continue.
-
Provide the following information for your application settings:
Field Description Name The name of your application. Grant type allowed You must enable Refresh Token. Base URIs Optional: The domain(s) of your application. Sign-in redirect URIs Redirect URL (e.g. https://${authenticate_service_url}/oauth2/callback).Controlled Access The user groups that can sign in to this application. See Group ID for more information. 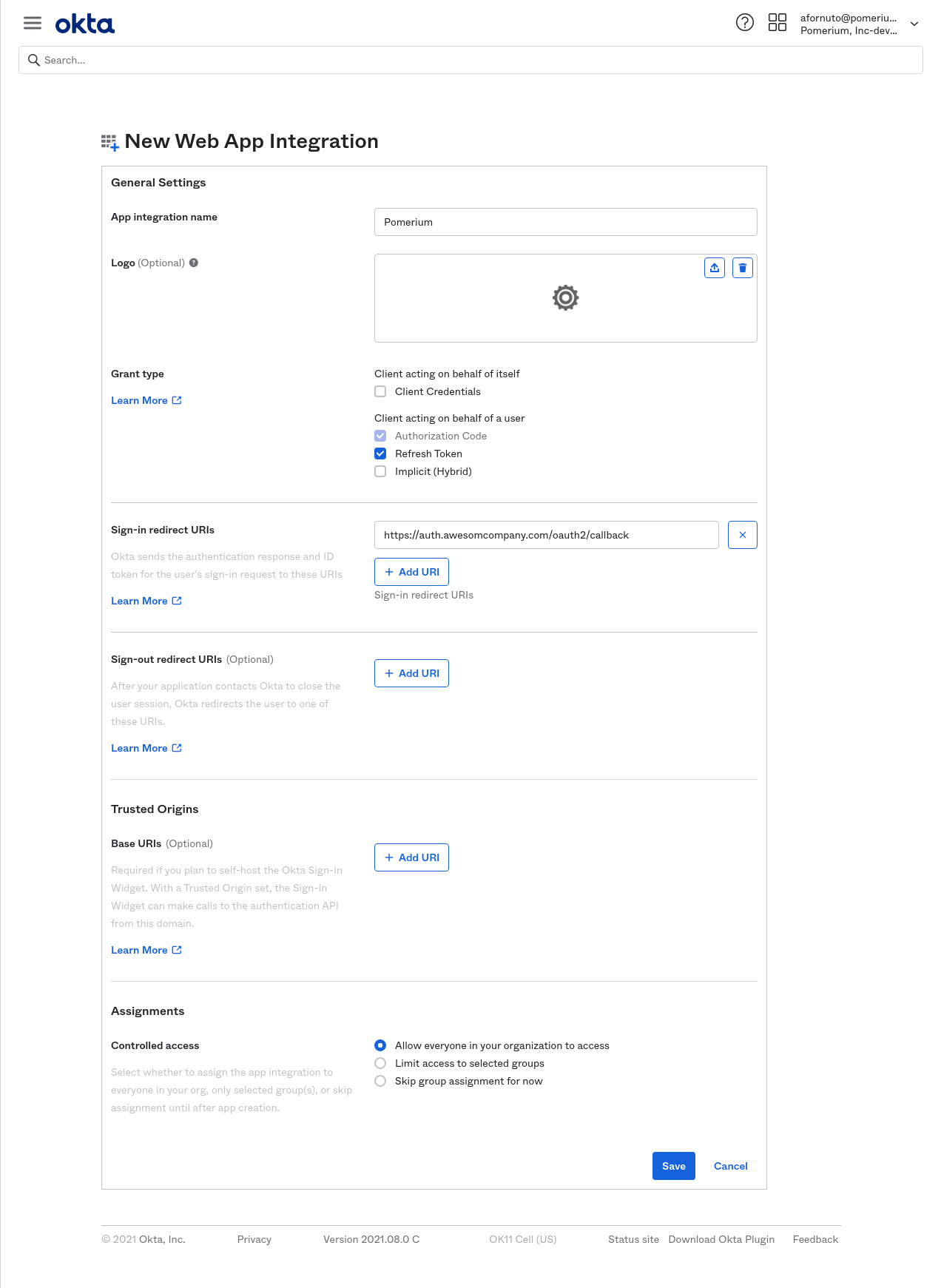
Click Save to proceed. You'll be taken to the General tab of your app.
-
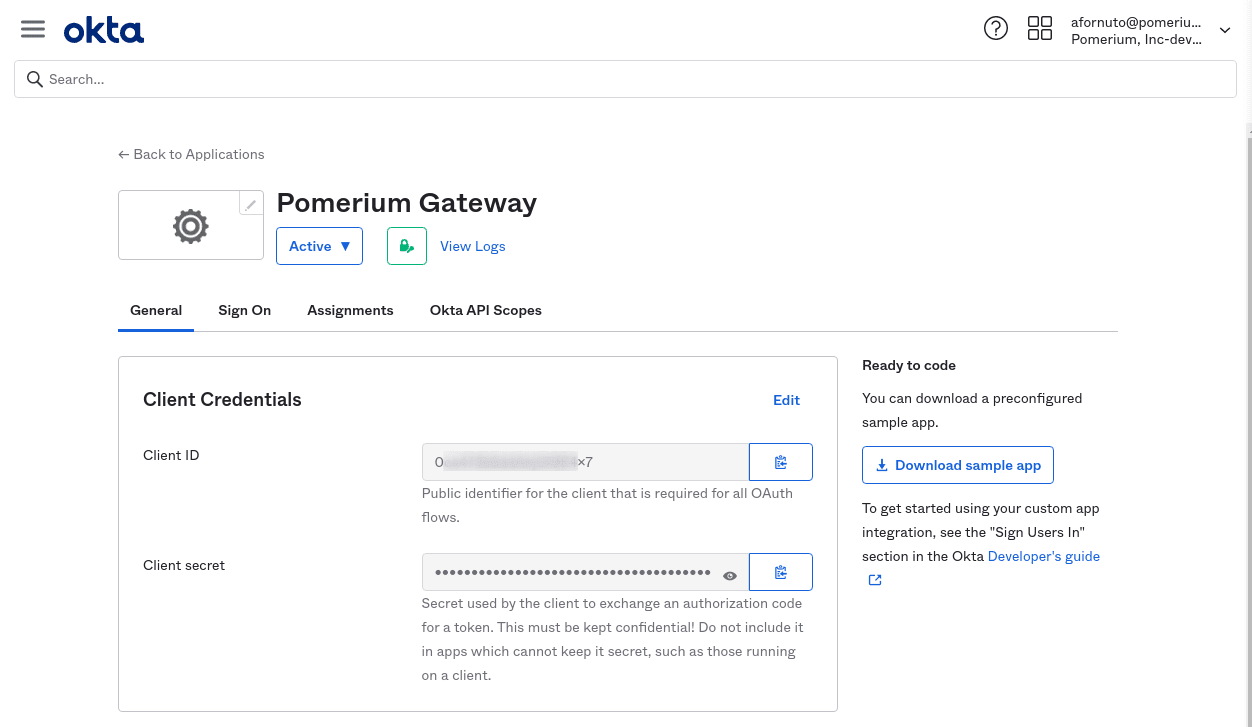
From the General tab, scroll down to the Client Credentials section. This section contains the Client ID and Client Secret. Temporarily save these values to apply to the Pomerium configuration.
Configure Pomerium
Finally, configure Pomerium with the identity provider settings retrieved in the previous steps. Your environmental variables should look something like this.
- config.yaml
- Environment Variables
idp_provider: 'okta'
idp_provider_url: 'https://awesomecompany.okta.com'
idp_client_id: 'REPLACE ME'
idp_client_secret: 'REPLACE ME'
IDP_PROVIDER="okta"
IDP_PROVIDER_URL="https://dev-108295.okta.com"
IDP_CLIENT_ID="REPLACE_ME"
IDP_CLIENT_SECRET="REPLACE_ME"
- Custom Claim (Open Source)
- Directory Sync (Enterprise)
Custom Claim (Open Source)
Groups
A groups claim can be added to tokens returned from Okta by following the Okta documentation.
Now when users login they will have a claim named groups that contains their groups and the claim PPL criterion can be used for authorization:
routes:
- from: 'https://verify.localhost.pomerium.io'
to: 'https://verify.pomerium.com'
policy:
- allow:
and:
- claim/groups: admin
Directory Sync (Enterprise)
Setting Up Directory Sync
Create an Okta Token
In order for Pomerium to validate group membership, we'll also need to configure a Token in Okta.
-
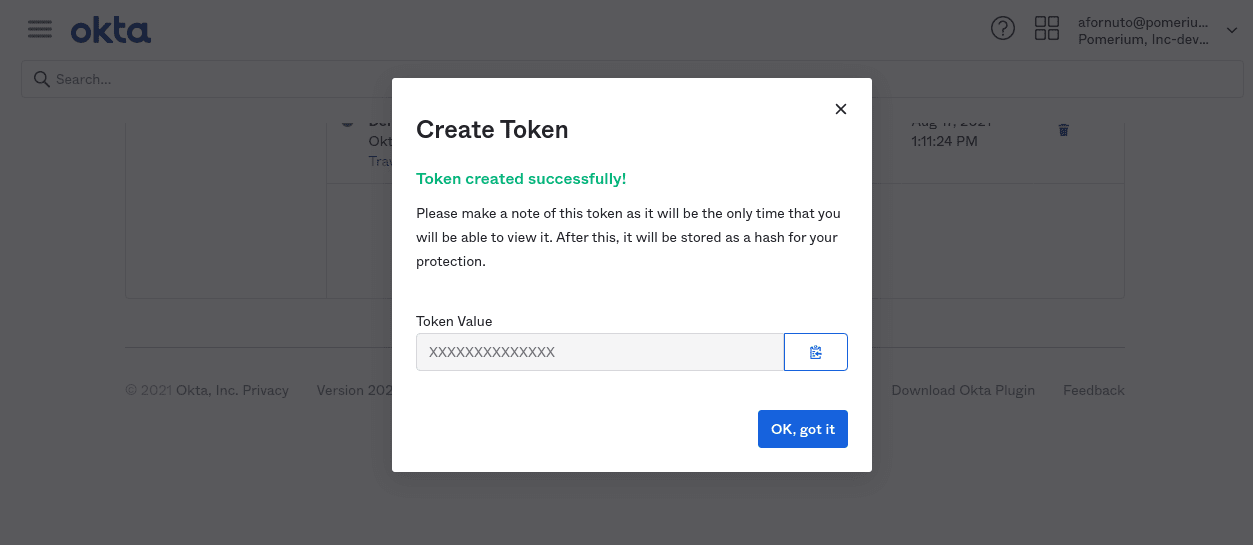
From the main menu, navigate to Security → API. Select the Tokens tab, and click the Create Token button. Name the token, then save the value to apply to our Pomerium configuration:
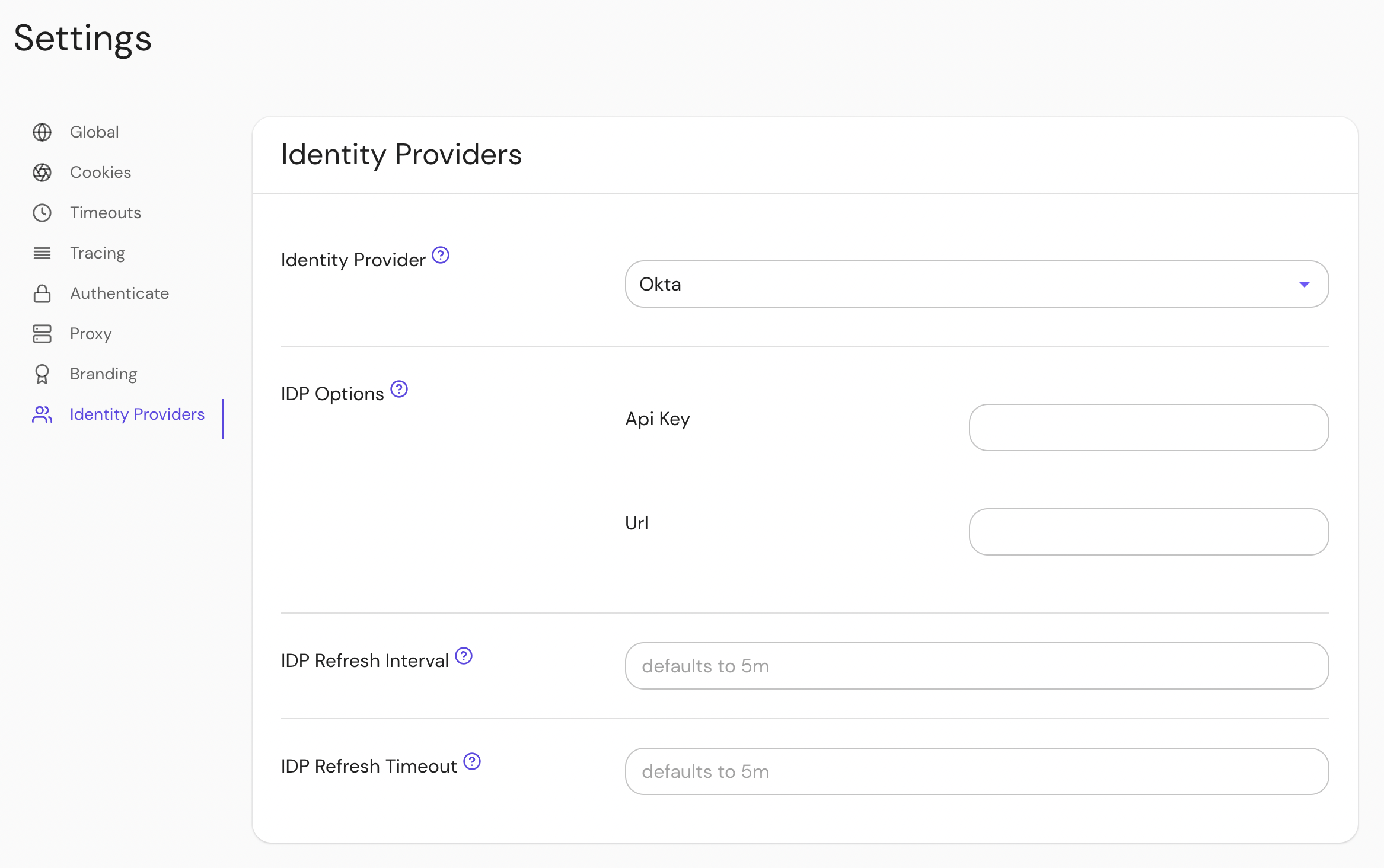
Configure Pomerium Enterprise Console
Under Settings → Identity Providers, select "Okta" as the identity provider and set the API Key and URL.